SandBlast Agent uses a fleet of threat engine technologies to help defend against the full scope of known and unknown zero-day malware. Here are some of the key threat prevention technologies and how they work:
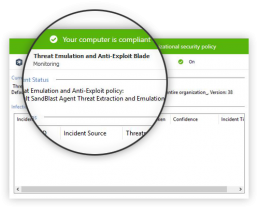
Threat Emulation / Threat Extraction
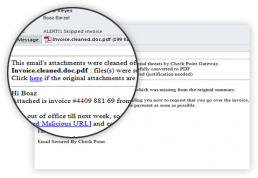
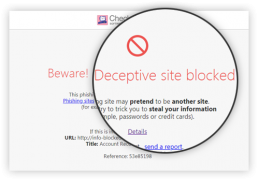
Zero-day Phishing Protection
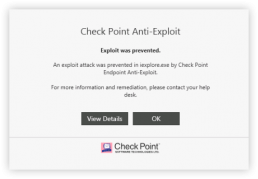
Every downloaded file using a web browser is put through threat emulation, or a sandboxing process where it is quarantined until deemed safe. Threat extraction ensures users receive “clean” files; the same downloaded file minus dangerous components. The sanitized, risk-free file can then be used normally, plus the option to access the original file.
Anti-Malware
Protect endpoints from unknown viruses, worms, and Trojan horse malware.
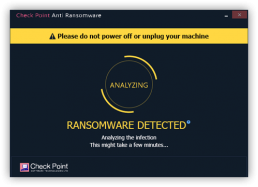
Anti-Ransomware
Monitors changes to files on user drives to identify ransomware behavior such as file encryption. Anti-Ransomware can also recover encrypted files regardless of the encryption used by taking smart snapshots of a user’s file when a change is being made to the file by an unknown application.
When a user browses a website and prior to typing in his/her credentials, the zero-phishing engine will inspect, identify, and block phishing sites. If the site is deemed malicious, the user will not be able to enter credentials. This engine offers zero-day protection based on site characteristics, such as known malicious URLs. Even brand-new phishing sites can be identified.
Advanced Threat Prevention
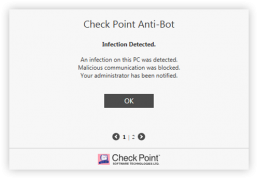
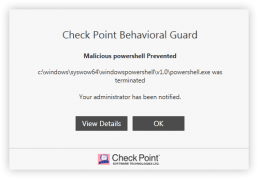
Anti-Bot detects and prevents communication by processes to malicious command and control server (C&C server) in the wild. Anti-Bot monitors all the network traffic coming from all the processes executed on the endpoint, and is able to detect malicious communication to C&Cs. Detection is based on two layers by comparing communication signatures to a known malicious communication signature and using Check Point Threat Cloud to identify malicious accessed IPs or domains.
Once a malicious communication is detected, Anti-Bot can block the communication immediately, kill the process, and put the process’s file in quarantine. A log is then sent to the log server to notify the system administrator.
Innovative Threat Prevention Technologies
Uses static, dynamic, and behavioral detection and prevention technologies with advanced artificial intelligence to provide high catch rates and low false positives.
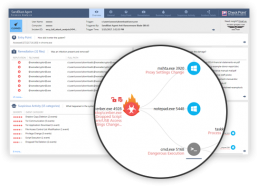
Insightful Detection and Response
Assures continuous collection of comprehensive and complete raw forensics data, employing full attack remediation capabilities.
Complete Endpoint Security Solution
Integrates into Check Point Infinity to get maximum prevention across all attack surfaces, shared intelligence, and a single point of management (cloud service or on premise).
SandBlast Agent Protects From Advanced Zero-day Malware
What happens if employees roam outside enterprise network that protect them from advanced zero-day invasions?
Set up a demo or POC (Proof of Concept)
Want to know more? Then contact us to organise a demo or set up a POC (Proof Of Concept).